So it’s been almost a year that I’ve switched to Gentoo Linux, and I’d like to share my experience with those that are curious and want to try it.
Gentoo Linux has a reputation in the Linux community for being the most hardcore Linux distribution there is, second to perhaps “Linux from Scratch”. This reputation is kind of well deserved because a Gentoo Linux user is not your typical Linux user. Essentially a Gentoo Linux user commits to building the entire operating system from scratch, including compiling the Linux kernel and customizing every little detail. Initial installation as a new Gentoo user can take some time as you are learning new things but eventually after you figured everything out it doesn’t take that long.
The main experience with Gentoo is all about learning, you get to learn basically a little bit of everything. If you are the kind of person that usually loses patience when something doesn’t work right, then Gentoo is probably not for you. But on the other hand, if you’re willing to invest the time to learn Gentoo then you will be greatly rewarded.
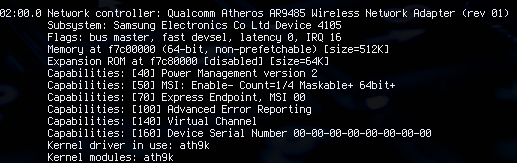
How will you be rewarded? Well that answer is relative. For example if you use a distribution like Ubuntu and you plugged in a brand new hardware, there’s a chance that the hardware might not work because support for that hardware is not available in the kernel.
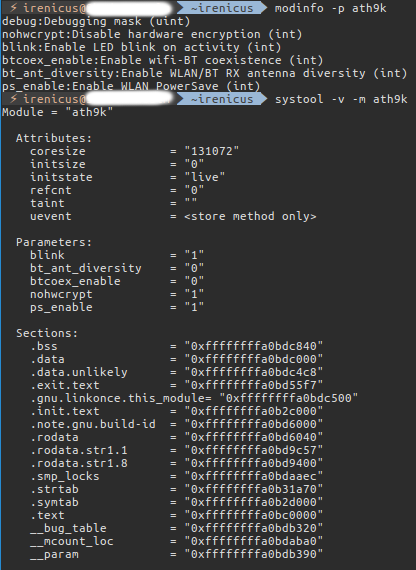
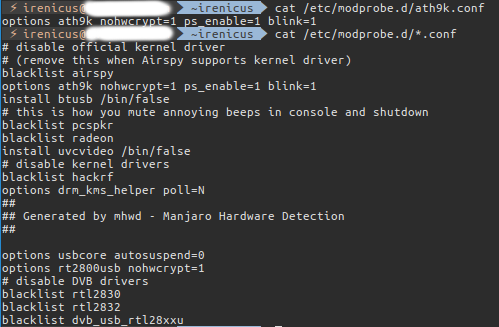
Perhaps your hardware requires a special firmware that needs to be downloaded manually and built into the kernel or may be a special FLAG needs to be set in the config file when you are manually compiling the kernel. If you have experience with Gentoo, you probably would be familiar with all these stuff and perhaps can fix the issues on your own for the most part. Thing is compiling the kernel is not as intimidating as it seems, as a Gentoo Linux user you get so used to compiling kernel that it becomes a habit. Sort of like drinking your morning coffee 🙂
Anyway, the point is investing the time in learning Gentoo is worth it. If you are using an Open Source Operating System like Linux, sooner or later you will definitely run into issues. That is just the nature of how things work in the Linux world 🙂
The skills that you pick up along the way as a full time Gentoo user are quite useful, so you can pretty much debug the hardware/software issues on your own without relying too much on the developers for support. Not to mention Gentoo forum is one of the best places for getting support. I’ve seen a lot of distributions for example Arch Linux where the community is very strict, you need to be careful when posting in Arch Linux forums as there’s strict rules related to forum etiquette and in general they are not as friendly to newbies. Compared to that Gentoo Linux community is welcoming and friendly to newbies.
Personally I’ve learned a lot using Gentoo, it made Linux fun for me again. At some point (in my early years as a Linux user) I was kind of disappointed with the Linux community because I was unable to debug and fix my hardware / software issues on distributions like Ubuntu. Filing bug reports and expecting them to get fixed was taking too long and I can’t really blame the developers because most of the contribution towards Open Source software is done by people on their free time and a lot of them don’t get paid for doing so. As I gained more experience I realized that it’s not actually them to blame but my mindset or to be more specific my lack of knowledge.
Linux is fun, it is exciting for the advanced users who have invested years learning it and have figured everything out. But at the same time it can also be quite frustrating and intimidating for the beginners. It is just a question of how much time you are willing to invest, either way it is worth it.